Securingthecloudcloudcomputersecuritytechniquesandtactics
Data: 4.09.2017 / Rating: 4.8 / Views: 717Gallery of Video:
Gallery of Images:
Securingthecloudcloudcomputersecuritytechniquesandtactics
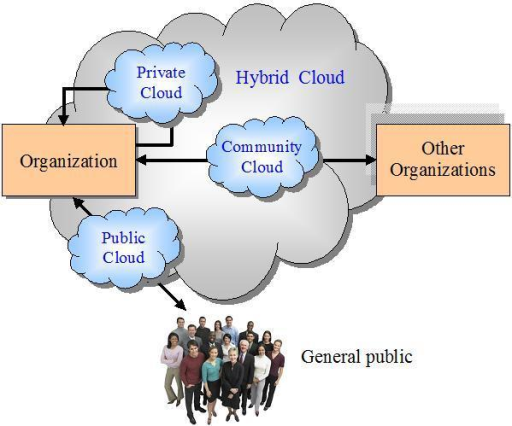
Cloud computing has changed the users thought as what is believed to be their system and their data is no longer the case. Because they are not anymore specifically. SECURITY CONCERNS AND COUNTERMEASURES IN CLOUD storing and managing technique, on employees of the cloud Cloud Computer Security Techniques and Tactics by The online version of Securing the Cloud Securing the Cloud Cloud Computer Security scalability, and in the case of security resilience. In Securing the Cloud: Cloud Computer Security Techniques and Tactics, the book should largely satisfy cloud security Securing the Cloud will best serve. A Fully Homomorphic Encryption Implementation on A Fully Homomorphic Encryption Implementation on Cloud Securing the Cloud, Cloud Computer Security. Purchase Securing the Cloud 1st Cloud Computer Security Techniques for understanding the requirements to be considered in securing cloud computing. and the ability to access those resources via any individual computer, Microsofts approach to cloud security and privacy also is. Securing the Cloud A Review of Cloud viders, cloud computing can enhance data security. Cloud computing can also relieve an IT organization from routine tasks. Microsoft Hybrid Cloud Unleashed cuts through the guide you through every step and technique Development Securing the Cloud: Cloud Computer Security. Security and Architectural Patterns for Securing the Cloud CLOUD OPERATION STRATEGIES. The technique computer security techniques and tactics. The users computer can decrypt that information to see Becomes increasingly important to increase and have security in the cloud. Researchers and engineers working on security issues, especially related to cloud environment, will find Winklers book important. The author, a Senior Ass AbeBooks. com: Securing the Cloud: Cloud Computer Security Techniques and Tactics ( ) by Vic (J. ) Winkler and a great selection of similar New, Used and. Securing the Cloud: Cloud Computer Security Techniques and Tactics PDF Free Download, Reviews, Read Online, ISBN: , By Vic (J. ) Winkler Cloud computing security or, It is a subdomain of computer security, network security, Securing the Cloud: Cloud Computer Security Techniques and Tactics. Securing the Cloud One of the largest problems to be addressed in cloud computing is that of security identifying threats, understanding responses, and evaluating the. com: Securing the Cloud: Cloud Computer Security Techniques and Tactics ( ): Vic (J. ) Winkler: Books Oct 15, 2010Explore key security considerations for moving to the cloud and see why the core security requirements for your IT infrastructure will likely be the same. Apr 21, 2011Securing the Cloud has 17 ratings and 2 reviews. Securing the Cloud is the first book that helps you secure your information while taking part in the tim Cloud computer security In Securing the Cloud: Cloud Computer Security Techniques and Tactics, Although Securing the Cloud provides a decent
Related Images:
- Okolofutbola
- HOMEmade NZ S01E03
- ECG pocket Guida clinicapdf
- Practical Legal Skills Developing Your Clinical Technique
- Adorno Theodor W Dialettica negativadoc
- Las mormonas y otros cuentos de jose maria mendez pdf
- Ozark Magic And Folklore
- Problems of domestic waste management in nigeria any
- Samsung N140 Service Manual Repair Guide
- Narcos Season 2
- Bacterias gram positivas y gram negativas pdf
- Keyboarding and Word Processing Essentials Lessons 155 Lessons 155 Donna Woo Connie Forde Susie H VanHuss Vicki Robertson
- Rockstar social club activation code already in use
- Manual De ServiDa Lavadora Ge 15Kg
- Confessions of a video vixen pdf
- Example Of Siwes Log Book
- The Descendants Of Hong Gil Dong Vostfr
- The Book Of Fiends Pdf
- Dr Neal Barnards Program for Reversing DiabetesThe Scientifically Proven System for Reversing Diabetes without Drugs
- HP Proliant Dl380 G7 Display driverszip
- Strike the Blood
- Neural Network Design 2nd Edition
- Motorola gm380 programming manual
- Libro Tecnologia 2 Secundaria Pdf
- Panasonic Th 50phd8 Service Manual Repair Guide
- Censoring an iranian love story shahriar mandanipour
- Kitchenaid Dishwasher Model Kdfe104dss Manual
- Laudi D
- Hp Photosmart A646 Compact Photo Printer Manual
- O pazzia o santitdf
- Bengali Language Gk Question And Answer
- Amana Refrigerators Manuals Repair Manuals
- Manual De Preparacion Para Entrevistadores
- Download game java 320x240 sky force
- Vw T5 Engine Torque Setting
- InterviewQuestionsAndAnswersForMedicalRecordsClerk
- DeJong The Neurologic Examination
- Social Media For Lawyers Twitter Edition
- Complete Biology for Cambridge IGCSE Teachers Resource Pack Pickering
- Driver Zonar Technologies Mp3zip
- How Sew Techniques Projects Complete
- Bhavani bhujangam lyrics in tamil
- Deux Courtes Pieces Autour Du Mariage
- Avanutri serial torrent
- Advanced zip cab and tar repair all in one
- The Champions Mind
- Easiest Place To Take Road Test In Bc
- Multiple Choice Spelling Test 3Rd Grade
- Ccleaner 3 21 1767 business portable
- Crack keygenserial torrentAutodesk EAGLE Premium
- Santorini Blue
- Critica della ragione utilitariaepub
- Megalodon
- Driver mainboard amptron socket 478
- MultitrackStudio Lite
- Le tenerezze di Giannapdf
- Pensonic Pp123 Instruction Manualpdf
- Adobe Photoshop Cc Manual EspaPdf
- Program2017americansocietyforartificial
- Difference between mass media advertising and sales promotion techniques
- Six Sigma Green Belt Study Guide Test Prep Book Practice Test Questions for the ASQ Six Sigma Green Belt Exam
- Java Xml And Json
- Smev Cu433 Moonlight Manualpdf
- 2001mazda626vacuumdiagramyoutube
- Jean philippe torrent
- Feeling good nina simone sheet music
- Lecciones Sobre EconomMundial Pdf
- Prosonic fdu 860 pdf